K.4.3 Case Where the Function Has Expired or is Disabled
K.4.3 Case Where the Function Has Expired or is Disabled
This section describes system operation and action to be performed when a CPU Activation Interim Permit expires or is disabled.
Configuration Example
The description here uses the following configuration as an example.
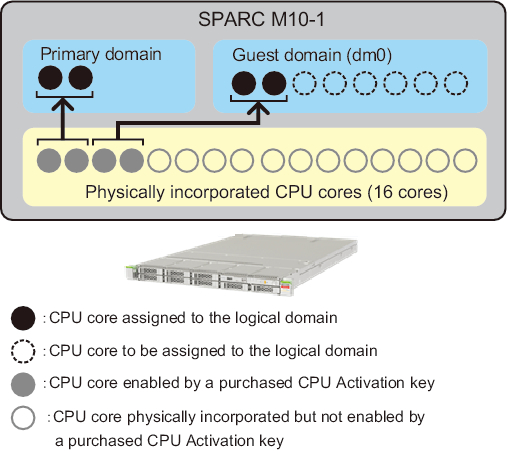
- Single CPU socket SPARC M10-1 with 16 physical CPU cores is used.
- CPU Activations to activate 4 CPU cores have been purchased and registered in the system.
- The system consists of two logical domains and they are running.
- - Two CPU cores are assigned to the control domain (primary domain).
- - Two CPU cores are assigned to the guest domain (dm0).
- To respond to a load increase, the guest domain (dm0) requires six more CPU cores.
- A CPU Activation Interim Permit is enabled, and six additional CPU cores have been assigned to the guest domain (dm0) as a temporary action.
|
Figure K-3 Configuration Example for the Case Where the Function Has Expired or is Disabled (SPARC M10-1)
|
|
| Note - CPU Activation keys registered in the system enable a definite number of CPU cores. They do not enable CPU cores by specifying the CPU socket and physical location of each CPU core. For the purpose of easy understanding, specific CPU cores are enabled and assigned to the logical domains in Figure K-3. |
System Operation and Action
The CPU Activation Interim Permit expires 30 days later regardless of whether additional CPU Activation keys are registered in the system. In addition, a CPU Activation Interim Permit may be disabled inadvertently by the setinterimpermit command of the XSCF. Once the CPU Activation Interim Permit is disabled, it cannot be enabled again with XCP 232x. Even with XCP 2330 and later, the function cannot be enabled again instantly then and there.
If the CPU Activation Interim Permit expires or is disabled when any CPU cores are in the use violation state "VIOLATION," the system operates in the following way.
- When 30 minutes elapse after the violation, a notification is sent to the system, which tries to delete excessive CPU cores from logical domains.
- When 60 minutes elapse after the violation, the system tries to shut down the control domain.
- When 90 minutes elapse after the violation, the system tries to shut down all domains.
If you perform either of the following operations within 30 minutes after the violation is detected, the system does not perform operations a. to c. above.
- - Reducing the number of CPU cores currently used in logical domains
- - Register additional purchased CPU Activation keys by using the addcodactivation command of the XSCF, and then adding the number of CPU Activations to the physical partition by using the setcod command.
If the CPU Activation Interim Permit expires and you execute the showinterimpermit command of the XSCF, "expired" will be displayed as shown in the following example.
| XSCF> showinterimpermit -p 0 Interim permit for PPAR 0: expired |
If the CPU Activation Interim Permit expires or is disabled and you execute the showcodusage command of the XSCF, the usage of CPU cores will be displayed as shown in the following example.
| XSCF> showcodusage -p resource Resource In Use Installed CoD Permitted Status -------- ------ --------- ------------- ------ PROC 10 16 4 VIOLATION: 6 cores in excess |
In this case, "VIOLATION" is displayed in the "Status" field because the CPU Activation Interim Permit has expired. The example shows that six CPU cores are used in violation, which actually warns the system of urgency. In the case of this example, you must immediately delete six CPU cores in total from logical domains.
After detecting a violation, the system tries to delete CPU cores from logical domains until the number of CPU cores in use matches the number of purchased and registered CPU Activation keys. Six CPU cores will be deleted in this example.
The system deletes CPU cores starting with the one with the highest CPUID (CID) value. The system may not be able to delete CPU cores for some reasons, such as that a vcpu belonging to the CPU core is associated with a specific process by pbind. In that case, the CPU core with the second highest CID value will be deleted.
You can check the CID value by using the ldm command from Oracle Solaris, as shown below.
| # ldm list-domain -o core NAME primary CORE CID CPUSET 0 (0, 1) 4 (8, 9) -------------------------------------------------------------- NAME dm0 CORE CID CPUSET 8 (16, 17) 12 (24, 25) <Omitted> |
After the number of CPU cores becomes equal to or less than the number of CPU cores whose use is permitted by purchased CPU Activation keys, the above action is not performed.
As mentioned above, deletion of CPU cores may fail. A failure of the deletion occurs when a vcpu is associated with a specific process by pbind or other means or when the CPU core to be deleted is the last one in a logical domain. If the system cannot delete enough CPU cores (six CPU cores in this case), the control domain will be shut down.
To recover from the above situation, perform either of the following operations.
- Delete enough CPU cores from logical domains by using the ldm command, or stop one or more logical domains.
- Register a sufficient number of purchased CPU Activation keys by using the addcodactivation command of the XSCF, and then add the number of CPU Activations to the physical partition by using the setcod command.
If enough CPU cores cannot be deleted due to shut down of the control domain, all logical domains will be shut down.
If all logical domains are shut down, possible recovery methods are as follows.
- Select the configuration information file of the logical domains that is saved before the CPU Activation Interim Permit is enabled.
- Select the old configuration information file of the logical domains by using the setdomainconfig command of the XSCF, as shown below. Then, boot the system.
| XSCF> setdomainconfig -p 0 PPAR-ID :0 Booting config (Current) :IPermit-enabled (Next) :IPermit-enabled -------------------------------------------------------------- Index :1 config_name :factory-default domains :1 date_created:- -------------------------------------------------------------- Index :2 config_name :before-IPermit domains :2 date_created:"2015-03-24 19:21:30" -------------------------------------------------------------- Index :3 config_name :IPermit-enabled domains :2 date_created:"2016-06-16 12:00:30" Select Index of Using config_name : 2 PPAR-ID of PPARs that will be affected :00 Logical domain config_name will be set to "before-IPermit". Continue?[y|n] :y |
- If your purpose is to recover the control domain, start only the control domain, and then delete the necessary amount of CPU core resources from the control domain.
| Note - Even if the number of CPU cores used in the control domain is greater than the number of CPU cores permitted for use by purchased CPU Activation keys, the control domain is always booted normally. The same applies even if the CPU Activation Interim Permit has expired or is disabled. However, if enough CPU cores cannot be deleted within 30 minutes after the detection of the violation, the system starts automatic deletion of CPU cores again according to the above procedure. After successful deletion of CPU core resources, save the corrected logical domain configuration information by using the ldm add-spconfig command so that it can be used in the future when the control domain is rebooted. |
- If your purpose is to recover a specific guest domain, perform the following procedure.
- 1. Boot only the control domain.
- 2. Delete CPU cores assigned to the guest domain from the control domain, and save the corrected logical domain configuration information by using the ldm add-spconfig command.
- 3. Boot the guest domain.
- Register additional purchased CPU Activation keys by using the addcodactiovation command of the XSCF, and add the number of CPU Activations to the physical partition by using the setcod command.
If you need to recover both the control domain and guest domain without using the old configuration information file of logical domains, both of the above operations b. and c. may be required.
< Previous Page | Next Page >